|
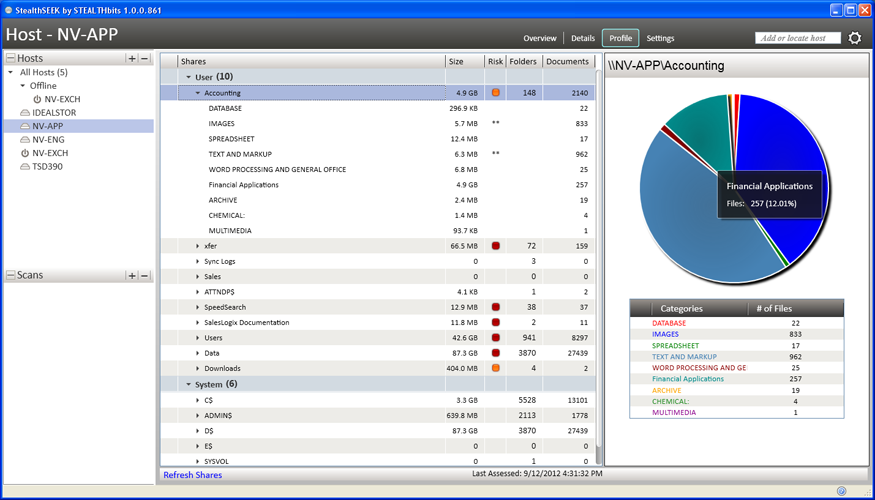
StealthSEEK identifies where sensitive data exists within File Systems
StealthSEEK is the ideal solution for identifying where unsecured, sensitive data exists within an organization's unstructured, unruly file systems. Whether scanning a desktop or Big Data stack, StealthSEEK is built to scale and classify content with surgical accuracy.
Across large distributed file systems, it's nearly impossible to keep track of the high-risk or sensitive data that is undoubtedly hiding in every corner of your network. A critical early step in any Data Governance program is the scanning of file systems to discover where high-risk or sensitive content may be buried deep within documents.
StealthSEEK offers a simple-to-deploy, easy-to-use alternative for identifying high-risk and sensitive information across your file systems. A lightweight data discovery solution that is both elegant and powerful, StealthSEEK was designed to begin producing answers just minutes after installation.
StealthSEEK identifies sensitive and high-risk data based on both common industry criteria (such as non-public or personal information, credit card data and Social Security Numbers) as well as enabling custom criteria that identifies data which is sensitive only to specific users or industries (such as intellectual property).
Successful Data Governance programs require an in-depth understanding of where sensitive and high-risk data resides across the network. StealthSEEK identifies risk associated with data exposure and takes the first-step in gaining control over unstructured data.
|