|
Share your USB security key between several machines over the network
| Publisher: |
Electronic Team, Inc. |
 |
| Downloads: |
1 |
| Software Type: |
Shareware, 19.99 |
| File Size: |
7.46M |
| OS: |
Windows All |
| Update Date: |
12 February, 2020 |
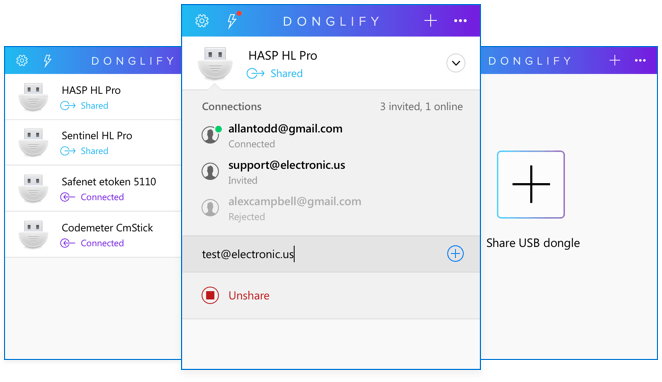
Donglify is a software tool that allows USB security keys to be shared over the Internet. Licensed USB dongles can be used and managed remotely by network-attached users. Advanced port redirection technology is employed to enable the dongle’s functionality to be forwarded to any environment with no distance limitations. All connections are fully secured by the program’s ability to perform 2048-bit SSL encryption. Donliify offers an efficient method of sharing USB dongles among multiple computers without requiring any additional software or hardware. There is no need for extra cable or hubs when sharing a security dongle with multiple users. When using the tool you just need to attach the dongle to a single machine and then share it over the network with any number of users connected to the same network. Note: The multi-connect function currently works with HASP HL Pro, Sentinel HL Pro, Sentinel UltraPro, SafeNet eToken 5110, and CodeMeter CmStick security keys. USB dongles of other types can be accessed from only one computer at a time. When you share a USB dongle with Donglify, remote users enjoy the same functionality achieved through a direct, physical connection to the device. The operating system on the remote machines recognizes the dongle as if it were locally attached. Another advantage of this software solution is the extended lifespan afforded the security keys by eliminating the physical wear on them caused by disconnecting and reattaching the devices to different computers. Just plug it into one computer and share it remotely to any PC with a network connection. It also provides a simple way to establish remote USB dongle access to virtual machine sessions. Donglify needs to be installed on the host computer as well as the guest operating system to enable the dongle to be shared. After installation, there are no limitations regarding the number or location of the virtual machines that can simultaneously access the device
|




